Configure PMM Server on AWS¶
Complete the essential security configuration, user management, and ongoing maintenance for your PMM Server deployment on AWS.
Prerequisites¶
Before configuring your PMM Server, ensure you have:
- completed planning your PMM Server deployment including instance sizing, storage, and network requirements
- successfully deployed PMM Server from AWS Marketplace
- completed the initial login and changed default credentials
- your PMM Server instance running and accessible via HTTPS
Secure your deployment¶
Configure SSL/TLS¶
Replace the self-signed certificate with a proper SSL certificate for production.
If you want to use a free Let’s Encrypt certificate:
- Make sure that the domain name pointing to your PMM Server IP.
- Check that port 80 temporarily open for certificate validation.
- Install and configure:
# Install certbot sudo apt update sudo apt install certbot # Stop PMM temporarily sudo docker stop pmm-server # Obtain certificate (replace yourdomain.com) sudo certbot certonly --standalone -d pmm.yourdomain.com # Configure PMM to use the certificate sudo cp /etc/letsencrypt/live/pmm.yourdomain.com/fullchain.pem /srv/pmm-certs/certificate.crt sudo cp /etc/letsencrypt/live/pmm.yourdomain.com/privkey.pem /srv/pmm-certs/certificate.key sudo chown pmm:pmm /srv/pmm-certs/certificate.* sudo chmod 600 /srv/pmm-certs/certificate.* # Restart PMM Server sudo docker start pmm-server
If you have a commercial SSL certificate:
-
Upload certificate files:
scp -i /path/to/your-key.pem certificate.crt admin@<instance-ip>:/tmp/ scp -i /path/to/your-key.pem private.key admin@<instance-ip>:/tmp/ -
Install certificates:
sudo mv /tmp/certificate.crt /srv/pmm-certs/ sudo mv /tmp/private.key /srv/pmm-certs/certificate.key sudo chown pmm:pmm /srv/pmm-certs/certificate.* sudo chmod 600 /srv/pmm-certs/certificate.* sudo docker restart pmm-server
Harden network access¶
Configure the operating system-level firewall on your PMM Server instance to further restrict access to required ports. This adds an additional layer of security beyond AWS Security Groups.
# SSH to PMM Server
ssh -i /path/to/your-key.pem admin@<your-instance-ip>
# Configure firewall rules
sudo ufw allow 22/tcp # SSH access
sudo ufw allow 443/tcp # HTTPS PMM interface
sudo ufw --force enable
Manage users and access¶
After the initial setup, create additional user accounts in PMM for your team members. Follow the principle of least privilege when assigning user roles.
- Go to Administration > Users and access > Users.
-
Click New user and configure the user with an appropriate role:
- Admin: Full system access
- Editor: Dashboard editing, no system config
- Viewer: Read-only access
-
Limit access based on job responsibilities and use viewer accounts for stakeholders who only need to see metrics.
Configure network and IP¶
By default, your EC2 instance will have a private IP for internal VPC network access. You can configure your PMM Server to use only a private IP or a static Elastic IP.
Use a private IP only¶
To use only the private IP for your EC2 instance during EC2 instance creation:
- In the Network Settings section, uncheck Auto-assign public IP.
- Do not assign an Elastic IP to the instance.
- To access PMM Server using only a private IP, ensure you’re connected to your VPC and use the private IP address for access.
To use only the private IP for an existing instance:
- If a public IP is assigned, remove it by disassociating it in the EC2 console.
- If an Elastic IP is assigned, disassociate it from the instance.
- To access PMM Server using only a private IP, ensure you’re connected to your VPC and use the private IP address for access.
Use an Elastic IP¶
For a static, public-facing IP address:
- Allocate an Elastic IP address in the EC2 console.
- Associate the Elastic IP address with your EC2 instance’s network interface ID.
Associating a new Elastic IP to an instance with an existing Elastic IP will disassociate the old one, but it will remain allocated to your account.
For detailed information on EC2 instance IP addressing, see the AWS documentation on using instance addressing.
Resize storage as needed the EBS volume¶
If more storage is required, increase the available disk space:
-
Your AWS instance comes with a predefined size which can become a limitation. To increase the size of the EBS volume attached to your instance, see Modifying the size, IOPS, or type of an EBS volume on Linux.
-
After updating the EBS volume, PMM Server will auto-detect changes within approximately 5 minutes and reconfigure itself.
Configure PMM Clients¶
Set server URL¶
Configure the PMM Server URL for client connections:
PMM_SERVER_URL="https://<elastic-ip-or-domain>:443"
PMM_SERVER_URL="https://<private-ip>:443"
Configure authentication¶
PMM Client authentication uses the same credentials you set for the web interface:
# Example PMM Client configuration command
pmm-admin config --server-insecure-tls --server-url=https://admin:your-password@<pmm-server-ip>:443
Test connection¶
Test PMM Client connectivity:
# Test PMM Server connectivity
curl -k https://<pmm-server-ip>:443/ping
# Expected response: "OK"
# Test API authentication
curl -k -u admin:your-password https://<pmm-server-ip>:443/v1/readyz
# Expected response: {"status":"ok"}
Set up RDS monitoring¶
To configure security groups for RDS access:
- Modify your RDS security group to add inbound rule: MySQL/Aurora (3306) from PMM security group.
- Test connectivity:
# From PMM Server nc -zv your-rds-endpoint.amazonaws.com 3306 - Add RDS instance in PMM using the RDS endpoint hostname.
Optimize memory allocation¶
To optimize memory allocation based on instance size:
# Check current memory usage
free -h
docker stats pmm-server
# For t3.medium (4GB RAM), adjust memory limits:
# Prometheus: 1GB, ClickHouse: 1GB, Grafana: 512MB
Back up and restore¶
To restore PMM Server from a backup:
-
Create a new volume using the latest snapshot of the PMM data volume:
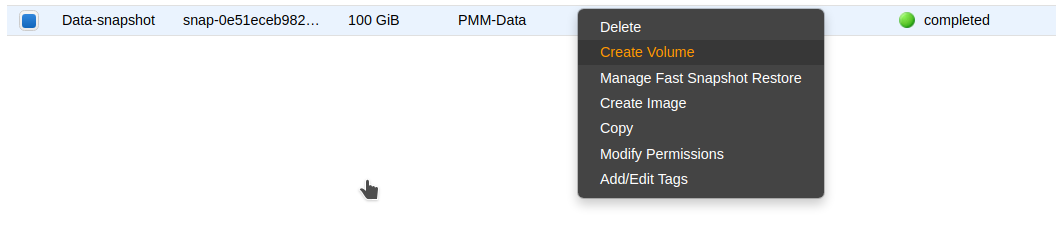
-
Stop the PMM Server instance.
-
Detach the current PMM data volume:
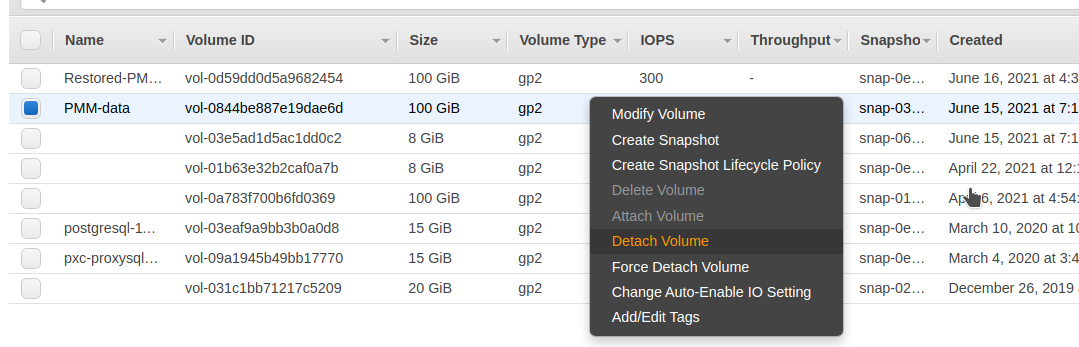
-
Attach the new volume:
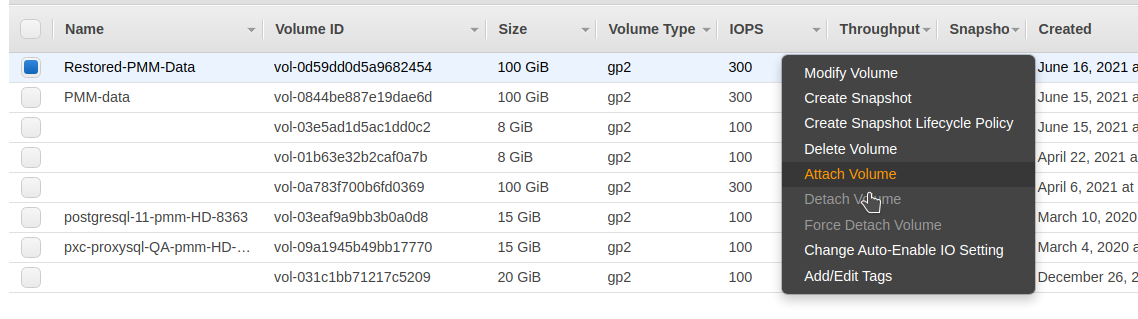
-
Start the PMM Server instance. The restore process typically takes 5-15 minutes depending on volume size and AWS region performance.
Remove PMM server from AWS¶
Data loss warning
Instance termination permanently deletes all data. Ensure you have completed all backup procedures before terminating an instance.
To permanently delete your PMM Server instance and clean up resources:
Use the AWS console for a visual, step-by-step termination process:
-
Go to the EC2 Console.
-
Find the instance you want to remove.
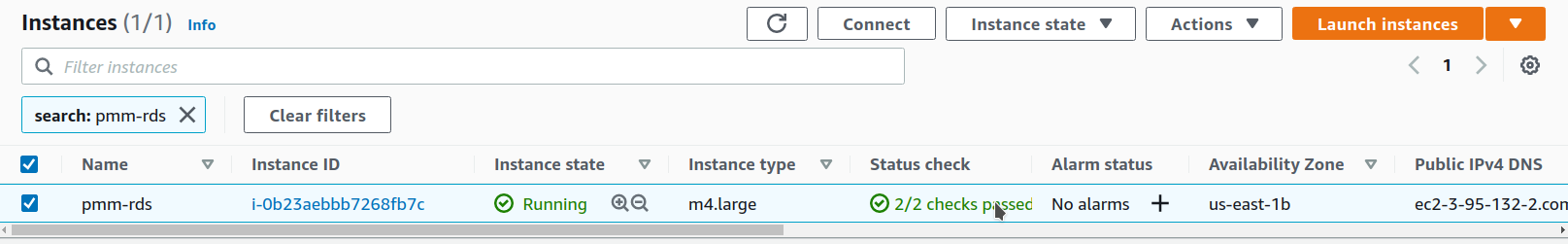
-
Open the Instance state menu and select Terminate instance.
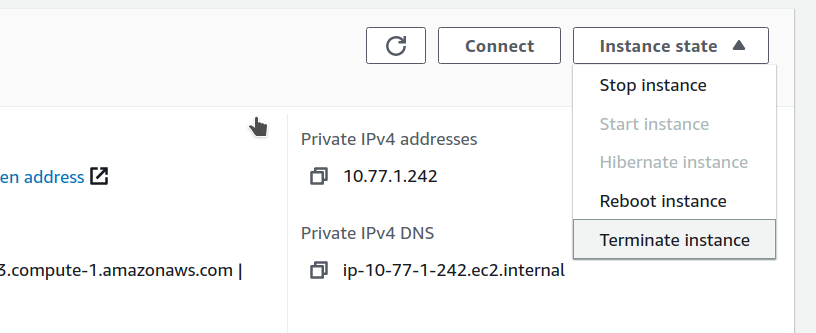
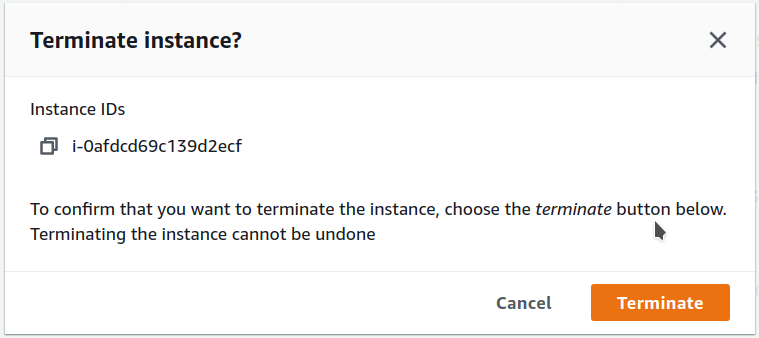
-
Confirm termination.
Use the AWS CLI when you want to automate termination with cleanup:
-
Create a final backup:
aws ec2 create-snapshot --volume-id $DATA_VOLUME_ID --description "Final backup before termination" -
Disconnect all PMM clients:
# On each monitored server pmm-admin remove --all -
Export configuration:
sudo docker exec pmm-server pmm-admin summary > pmm-final-config.txt -
Stop PMM services:
sudo docker stop pmm-server -
Terminate the instance:
aws ec2 terminate-instances --instance-ids i-1234567890abcdef0 -
Clean up AWS resources (optional):
# Release Elastic IP if allocated aws ec2 release-address --allocation-id eipalloc-12345678
Next steps¶
With your PMM Server fully configured and secured:
- Configure PMM clients to start monitoring your infrastructure
- Register client nodes with your PMM Server
- Configure SSL certificates for production use
- Set up monitoring alerts for proactive monitoring